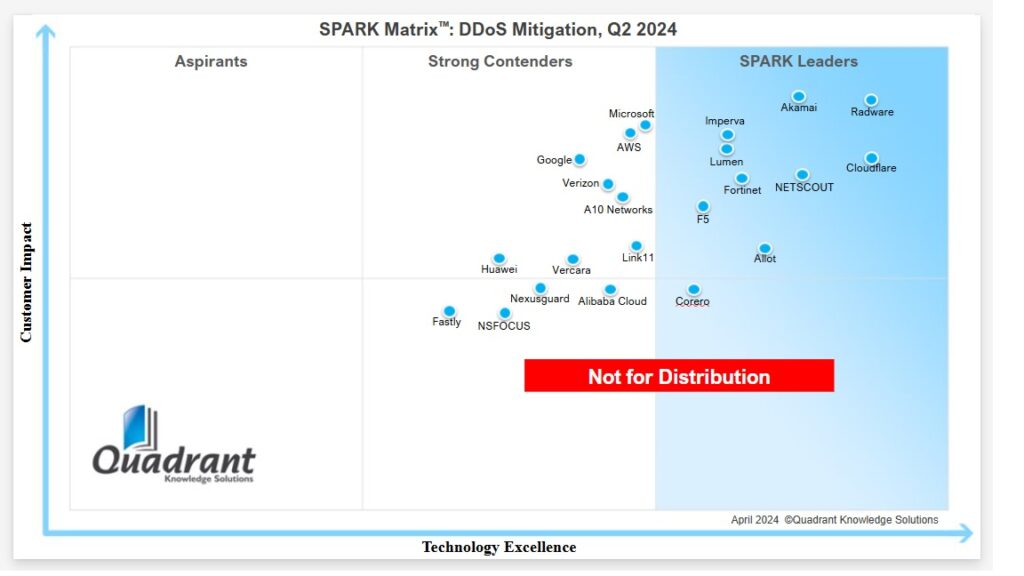
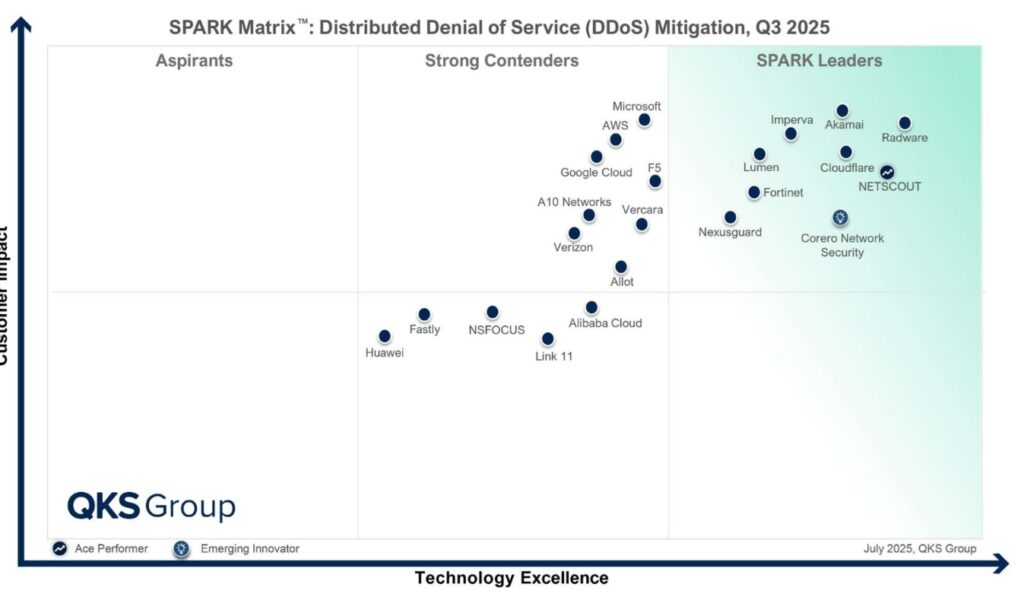
Despite everyone’s best efforts, DDoS attacks continue to be a nuisance. The emergence of new technologies like AI has allowed bad actors to add teeth to the attacks. Having a DDoS mitigation tool as a part of the security stack is a necessity, not an option. But buying the right product is also a critical process. The product should provide reasonable, if not great, ROI. Matrices comparing various products based on several factors, like customer impact, are a great help in choosing a product that meets your specific requirements. A year-on-year comparison of two matrices helps you refine your search. So, here is the comparison of SPARK Matrices of 2024 and 2025 for the DDoS mitigation software market.
Market situation
We can infer that the DDoS mitigation market is consolidating by looking at the two matrices given above. There is a clear cluster of leaders that are way ahead of any competitors. In addition, the number of players has clearly reduced in 2025.
The class toppers
Akamai, Radware, Fortinet, Lumen, Imperva, NETSCOUT, and Cloudflare are the leaders. The quadrant contains a mix of companies that remain high on both axes, offering mature, globally distributed platforms and steady performers with a balance of scale, technology, and customer satisfaction. These providers show sustained innovation and customer trust, making them safer bets for long-term deployments.
The contenders
The contenders’ quadrant includes some of the industry giants, such as Microsoft, Amazon, and Google. The other vendors are Verizon, Vercara, F5, Huawei, Fastly, NSFOCUS, Link11, A10 Networks, Alibaba Cloud, and Allot. These vendors are steadily improving but are still outside the leader quadrant zone in both reports. These vendors may offer integrated, lower-friction solutions and solutions that are good for businesses seeking focused DDoS expertise while avoiding the cost factor of top-tier solutions.
The ranking
| # | Vendor | 2024 Position | 2025 Position | Movement & Likely Reason |
| 1 | Akamai | Leader | Leader | Held top-right spot thanks to global edge network and very large scrubbing capacity. |
| 2 | Cloudflare | Leader | Leader | Continued growth in enterprise and SMB markets; strong bundling of WAF/bot/CDN kept customer impact high. |
| 3 | Radware | Leader | Leader | Ongoing hybrid protection and behavioural algorithms → steady performance. |
| 4 | Imperva | Leader | Leader | Stable position; benefits from coupling DDoS with web & API protection. |
| 5 | Lumen | Leader | Leader | Leverages backbone and scrubbing centres; constant carrier appeal. |
| 6 | NETSCOUT | Leader | Leader | Arbor platform improvements & telco analytics earned an “Ace” note in 2025. |
| 7 | Fortinet | Leader | Leader | Integration with security fabric preserved rank. |
| 8 | Corero Network Security | Leader | Leader | Real-time inline technology gained stronger visibility. |
| 9 | F5 | Leader | Strong Contender | Out of the leader quadrant; remains good for appliance/hybrid scenarios. |
| 10 | Allot | Leader | Strong Contender | Dropped a tier; suggests slower roadmap or narrower focus vs cloud-first vendors. |
| 11 | Microsoft (Azure DDoS) | Strong Contender | Strong Contender (slightly higher) | Incremental gains in Azure DDoS; still positioned as an add-on rather than a standalone leader. |
| 12 | AWS (Shield) | Strong Contender | Strong Contender | No change in position. Product is excellent for AWS-hosted apps. |
| 13 | Google Cloud (Cloud Armor) | Strong Contender | Strong Contender (a bit higher) | Application-layer features improved customer impact, but not enough to jump tiers. |
| 14 | Verizon | Strong Contender | Strong Contender | Managed SOC model remains steady; no major placement change. |
| 15 | Vercara (ex-Neustar) | Strong Contender | Strong Contender (shifted up/right) | Branding & service analytics boosted perceived technology strength. |
| 16 | A10 Networks | Strong Contender | Strong Contender | Steady product strong in appliances but slower cloud pivot. |
| 17 | Link11 | Strong Contender | Strong Contender (lower) | Same quadrant but moved slightly down/left, reflecting limited global scale. |
| 18 | Huawei | Strong Contender | Strong Contender (lower) | Market/geopolitical limits constrained customer reach. |
| 19 | Alibaba Cloud | Strong Contender | Strong Contender (lower) | Retained role for Asia workloads but not global parity. |
| 20 | NSFOCUS | Strong Contender | Strong Contender (lower) | Remains at the same tier as global competitors accelerate the addition of cloud-native features. |
| 21 | Fastly | Strong Contender | Strong Contender (lower) | Refocused on broader edge delivery, deprioritising dedicated DDoS. |
| 22 | Nexusguard | Strong Contender | Leader | Clear upward move: heavy ISP/MSP focus & SOC services raised tech and impact ratings. |
Buyer advice
So, which DDoS mitigation product should you consider? Organizations with mission-critical services with worldwide reach should consider consistent leader vendors: Akamai, Cloudflare, Radware, Imperva, Lumen, NETSCOUT, Fortinet, and and Corero. These vendors provide combine massive scrubbing capacity, robust SLAs, and proven resilience against high-volume attacks. They are the safest choice when service continuity and latency control are non-negotiable.
Service and managed protection providers benefit from DDoS mitigation solutions built for multi-tenant environments and continuous SOC operations. Nexusguard, which advanced from Strong Contender to Leader in 2025, is a prime candidate for managed protection at scale. NETSCOUT and Corero also stand out for inline detection and carrier-grade visibility.
Hybrid environments and appliance-heavy networks balancing data centre and cloud workloads, or requiring appliances integrated with firewalls/load balancers should consider Fortinet, F5, A10 Networks, and Allot.
Native options like AWS Shield, Azure DDoS Protection, and Google Cloud are good for cloud-native workloads. These DDoS mitigation tools provide simple activation, tight platform integration, and predictable billing. They are also most effective when protecting assets hosted entirely inside their respective ecosystems.
Regional or budget-sensitive enterprises should consider contenders like Link11, Alibaba Cloud, Huawei, NSFOCUS, Fastly, Vercara, and A10 Networks. These vendors’ DDoS mitigation offerings suit organizations with localized latency requirements, moderate risk profiles, or cost constraints. While they may not match the scrubbing levels offered by the leaders’, they can deliver solid protection in targeted contexts.
Final word
The comparison of the two matrices shows the DDoS mitigation market is consolidating, which can be seen by the fact that most of the leaders have not only retained their spots but have improved their positioning. The DDoS mitigation market landscape is evolving rapidly, driven by more sophisticated attacks and the need for scalable, cloud-native defense. Along with the matrix, buyers should select the best-fit DDoS mitigation product by considering business priorities, cloud footprint, performance expectations, and vendor stability.
Click here for the 2023-2024 comparison. Click to read/access the 2024 and 2025 reports.

