Microsoft defines a Service Account as “A service account is a user account that’s created explicitly to provide a security context for services that are running on Windows Server operating systems. The security context determines the service’s ability to access local and network resources.” Yet, they can be compared to the (false) stereotype of the “quiet kid in the school.” They are rarely discussed in boardrooms, seldom included in transformation roadmaps, and almost never part of employee lifecycle conversations. Yet when breaches are investigated, these accounts often emerge as vectors.
Why service accounts sprawl (and become un-disableable)?
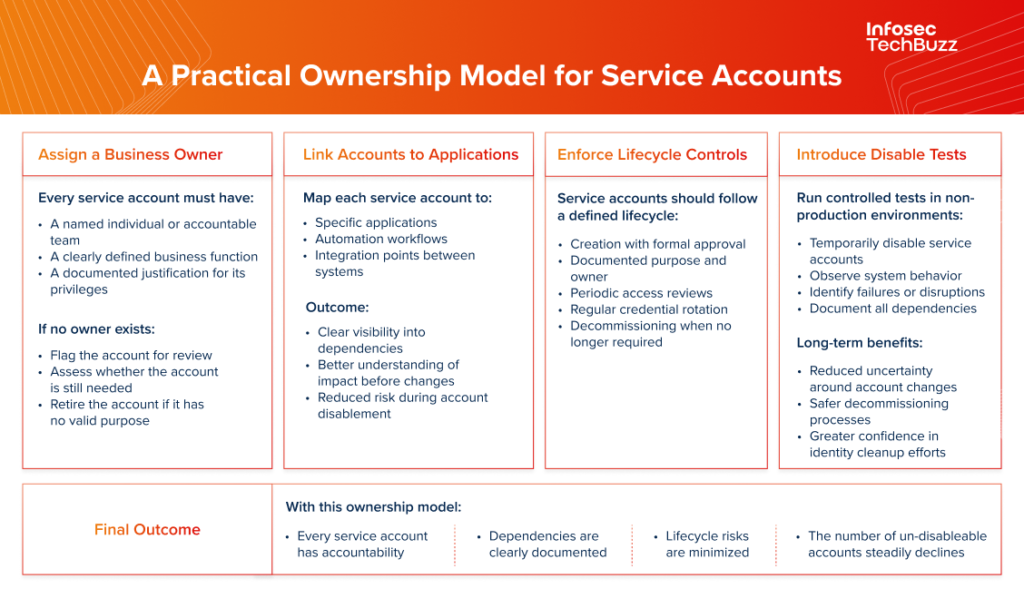
Service accounts are essential for automation. Modern tech environments depend on background processes such as application-to-application communication, API integrations, batch processing, monitoring tools, and patch management. These processes need identities, and service accounts provide them. However, service accounts also typically do not have interactive logins, are not tied to individual employees, and run continuously or on schedules, unlike human IDs. They also often have elevated privileges and are created for technical convenience rather than governance clarity. As environments evolve because of factors like mergers, new SaaS tools coexisting with legacy systems, automation scripts, and temporary integrations, all of them contribute to identity sprawl. In many enterprises, the number of service accounts rivals or exceeds the number of human users. Yet they rarely undergo the same level of scrutiny. And this can lead to situations where these accounts cannot be deleted or disabled.
This situation arises because of a combination of technical dependencies and ownership gaps. Many are created without a clear business owner, embedded deep inside critical workflows, or hard-coded into legacy applications and scripts. Over time, the same account may be shared across multiple systems, its credentials left unchanged for years, and its dependencies undocumented. In some cases, vendor or legacy system constraints prevent easy changes, while the absence of test environments makes teams reluctant to experiment. The result is an account that no one fully understands or owns, and disabling them may end up disrupting essential operations. So, the problem here is not the account, but the absence of any sort of ownership of it. The “bad actors” obviously love such situations.
Pheromones for cybercriminals
Service accounts are attractive targets because they often have broad, persistent privileges, are not subject to multi-factor authentication, rarely trigger alerts when used, may not have password rotation policies, and operate outside normal user behavior analytics. Once compromised, these accounts can provide long-term, low-visibility access to critical systems. Also, security teams tend to focus on controls such as password rotation, privilege reduction, monitoring, and vaulting. These measures, while necessary, address symptoms, not the causes. An account that no one owns will eventually become an account that no one can disable. In that sense, un-disableable service accounts are not just technical artifacts. They are organizational signals that point to unclear accountability, undocumented dependencies, and governance gaps.
Sanket Kadam, Senior Security Analyst at QKS Group, explains, “Un-disableable service accounts highlight a structural governance gap rather than a purely technical weakness. When machine identities lack clear ownership, documented dependencies, and lifecycle oversight, they evolve into persistent risk vectors with elevated privileges and low visibility. The article correctly frames service account sprawl as an accountability failure rooted in operational convenience and legacy complexity. Organizations that treat nonhuman identities as governed assets, with ownership, attestation, and lifecycle controls, can significantly reduce latent access risk. The emerging vendor focus on machine identity governance underscores a broader shift toward identity-centric security operating models.”
Vendor landscape shift
Modern identity security platforms are beginning to treat service accounts as first-class identities rather than background artifacts. Vendors such as CyberArk, BeyondTrust, Delinea, and One Identity are expanding capabilities around privileged service account discovery, automated credential rotation, dependency mapping, and least privilege enforcement. Identity governance platforms from vendors such as SailPoint, Saviynt, and Omada are also incorporating service account attestation, ownership workflows, and lifecycle management for nonhuman identities. This situation indicates that vendors (and users) are now realizing that machine identities outnumber human users in many environments and require comparable governance.
In the end….
Service accounts become time bombs when left ownerless. Once every service account has a clear owner, a defined purpose, and a lifecycle, the idea of an un-disableable account begins to disappear, along with one of the quietest but most persistent risks in enterprise identity security.

