Going by their ubiquity, we can safely say that the API economy is booming. The APIs allow systems to connect rapidly and seamlessly. This ability has enabled collaboration between companies, developers, and consumers and created new opportunities for innovation, efficiency, and revenue generation. The ability has also made APIs a target for bad actors. A compromised API provides various “benefits,” including access to sensitive data and logic, and access to even more APIs, expanding the attack surface exponentially. That brings us to the point: How secure are your APIs, really, and how quickly can we do an API risk audit without needing the presence of full-time AppSec specialists?
Importance of API security
As we have stated above, the ubiquitousness of APIs also means they are fast becoming vectors for data exposure. Here are some notable incidents where API vulnerabilities led to the exposure of sensitive data like Personally Identifiable Information (PII):
1. Intel employee data exposure: As if Intel’s present issues are not enough, the data of about 270,000 employees was exposed because of dodgy APIs. The data included names, roles, contact details, and sensitive company hierarchy data.
2. Microsoft Azure: This flaw, deemed critical, allowed users to mint privilege tokens. It left data like names, contact information, job titles, and complete directory structures exposed. The flaw, fortunately, was not exploited in the wild.
While these two incidents are among latest ones, the list is incomplete for length’s sake. There are more such incidents.
QKS Group’s Senior Application Deployment Analyst Ipsita Chakrabarty outlines the need for securing APIs. “In today’s interconnected landscape, APIs are the arteries of digital ecosystems and their most exposed surfaces. Securing them isn’t just a security function; it’s a business imperative. A one-hour threat modeling exercise may seem brief, yet it can uncover blind spots that often go unnoticed for months. The goal isn’t perfection in sixty minutes, but awareness because you can’t defend what you don’t understand,” Ipsita advises.
The threat audit checklist
Below is a table outlining typical operations performed during a one-hour API threat model audit. Each stage is tailored to maximize coverage and effectiveness within an hour, focusing on high-impact and actionable checks.
| Time (Minutes) | Operation | Description |
| 0–5 | Kickoff & Scope Definition | Clarifying audit goals, assets, and boundaries: deciding the API(s), endpoints, and sensitive operations that are to be reviewed. |
| 5–10 | Asset & Endpoint Enumeration | Identifying all documented and undocumented API endpoints, data flows, and integration points. |
| 10–15 | Authentication & Authorization Review | Verifying OAuth2, API keys, JWT, RBAC, and test for misconfigurations, weak tokens, or missing authorization. |
| 15–20 | Input Validation & Injection Protection | Checking request parameters, validating input controls, and testing for SQL/command injection and parameter tampering risks. |
| 20–25 | Rate Limiting & Resource Protection | Assessing the implementation of rate limits, throttling, and protections against Denial of Service (DoS) or abuse. |
| 25–30 | Data Exposure & Privacy Assessment | Analyzing API responses for sensitive data leakage, unnecessary information, and encryption in transit (TLS checks). |
| 30–35 | Logging & Monitoring Setup Check | Confirming audit logging is enabled, authentication events are recorded, logs are protected, and SIEM integration if relevant. |
| 35–40 | Dependency & Third-Party Review | Reviewing API dependencies, libraries, and integration points for unpatched vulnerabilities or insecure third-party services. |
| 40–45 | Error Handling & Reporting Controls | Testing for detailed error responses that may leak technical details or enable enumeration and evaluate monitoring of critical errors. |
| 45–50 | Business Logic & Abuse Testing | Performing quick checks for logic flaws, including privilege escalation, excessive function exposure, or broken workflow protections. |
| 50–55 | Documentation & “Zombie” Endpoint Check | Checking for outdated, undocumented, or deprecated endpoints that may be externally accessible or misconfigured (“zombie” APIs). |
| 55–60 | Reporting & Recommendations | Summarizing key findings, prioritizing actionable remediation steps and providing a concise executive-level summary of security posture. |
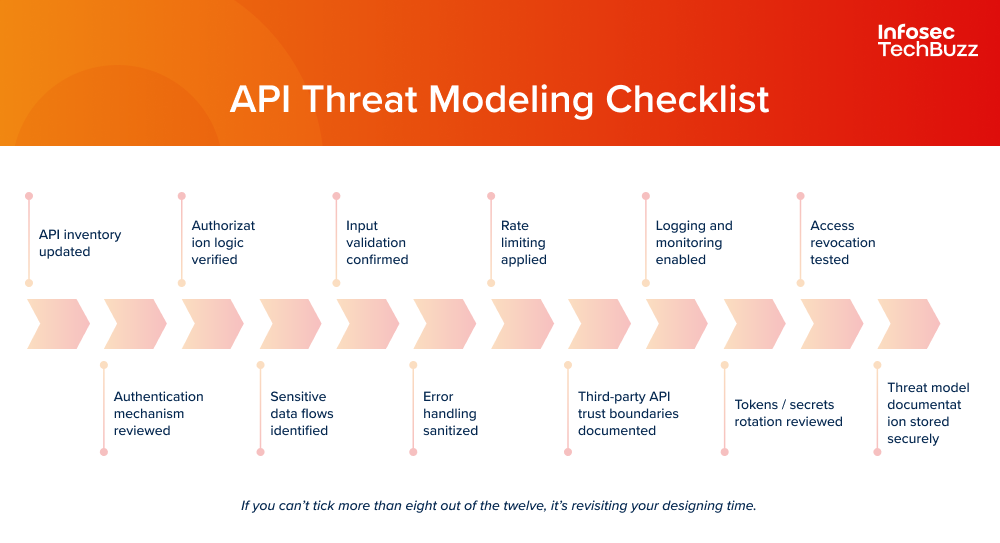
Let’s break down each step, describing their goal and importance.
1. Kickoff & Scope Definition (0–5 min)
The checks kick off with establishing the most critical assets that are to be reviewed, including APIs (internal, external, public), endpoints, and assets. The process includes gathering documentation, discussing goals with stakeholders (if available), and setting boundaries for what will be covered. This process helps prevent wasted effort and ensure that key areas are not missed.
2. Asset & Endpoint Enumeration (5–10 min)
This part involveslisting all API endpoints (public and private), including the documented and the ones discovered through tooling or logs. It involves documentation review, inspection of traffic through tools like Postman and Swagger, and scanning for hidden or deprecated endpoints. Protecting APIs you don’t even know exist is impossible and missing endpoints are common attack targets.
3. Authentication & Authorization Review (10–15 min)
This step is tocheck that only legitimate users/applications can access endpoints and that permissions are strict. It reviews how authentication is handled (e.g., OAuth2, API keys), check configuration, test for bypass or weak controls, and ensure proper role-based restrictions. This step is critical as broken authentication/authorization is a leading cause of API breaches.
4. Input Validation & Injection Protection (15–20 min)
This step helpsprevent attackers from sending malicious input (e.g., SQL, OS commands) through the API. it involves checking if the API sanitizes or validates incoming parameters and payloads, test for injection vulnerabilities because weak validation makes APIs susceptible to various types of attacks, such as SQL injection, XSS, and command injection.
5. Rate Limiting & Resource Protection (20–25 min)
This step is toensure controls are in place to prevent abuse, DoS attacks, and resource exhaustion.It involves testing of rate limits by sending many requests quickly and check if throttling is applied and properly configured. It is needed as absence of rate limits allows even the bad actors to overwhelm even legitimate endpoints to cause outages.
6. Data Exposure & Privacy Assessment (25–30 min)
This step is performed to limit the data returned by the API to only what’s necessary for users. it includes review of example responses and checking for unnecessary sensitive data, unencrypted information, and validate TLS/HTTPS use.These steps are necessary as overexposed data is a prime target for attackers and can lead to compliance issues.
7. Logging & Monitoring Setup Check (30–35 min)
This step is performed to ensuresecurity-relevant events are logged, monitored, and protected. It involves checking if authentication, access, and errors are logged, verifyig logs are not exposed and reviewing monitoring integrations. Good logging helps detect and investigate security incidents quickly.
8. Dependency & Third-Party Review (35–40 min)
This step is to Identify risks from libraries, SDKs, and external services used by the API. It involves making a list of dependencies, checking for latest versions, and reviewing them for known vulnerabilities. Vulnerabilities in third-party code or outdated services can be exploited as attack vectors.
9. Error Handling & Reporting Controls (40–45 min)
This step is to checkAPIs to prevent them from leaking sensitive information via error messages. This is done by triggering errors intentionally and review messages for details such as stack traces and config values that could aid attackers. Verbose errors are often used for reconnaissance during attacks.
10. Business Logic & Abuse Testing (45–50 min)
Check for logical vulnerabilities (e.g., BOLA/BFLA) that don’t require traditional exploits. It includesattempting abnormal or privilege escalation actions such accessing other users’ data when not permitted. While APIs are often assumed secure technically, logical flaws remain common and impactful.
11. Documentation & “Zombie” Endpoint Check (50–55 min)
This step is performed tocheck for outdated, undocumented, or orphaned endpoints. It is performed by comparing deployed APIs versus documentation and checking for endpoints no longer used but still exposed. “Zombie” endpoints are often left unmonitored and unpatched, making them attractive attack vectors.
12. Reporting & Recommendations (55–60 min)
This is the final step where yousummarize findings, prioritize fixes, and communicate risks to technical/business stakeholders and present a short summary highlighting critical issues, recommended remediations, and next steps. It is needed as clear communication helps ensure quicker action and improve your organization’s overall security posture.
Final Word
In today’s increasingly integrating and complex-er network environments, APIs allow you to connect a myriad systems. In the wrong hands, they become a hazard which can be solved only by disconnecting systems. This handy checklist will ensure that the matters never escalate to the disconnection stage.

